Your guide to RFID Security - RFID Blocker Card to protect your information
Concerned about contactless card or passport skimming? Our article dives deep into the risks of RFID scanning and how you can protect your information. Learn how RFID blocking card or RFID blocking sleeve creates a shield around your credit cards, preventing unauthorised scans and stopping thieves in their tracks. Read now and keep your cards and travel documents safe!
Travel Cybersecurity: Privacy & Security on the Go
As security professionals, we understand the risk travel poses to your digital data. Drawing on the insights of security experts, we've compiled a list of the best travel security tips to keep you safe on your adventures.
How Do Microphone Blockers Work?
With microphones built into many devices, people worry about them on their phones, laptops, and other equipment. But can you disable them with a microphone blocker? Like many things in cybersecurity, the answer is a nuanced "it depends." This post explores the challenges and potential solutions for silencing your microphone, empowering you to take back control of your privacy.
Cyber Security Risk Sources Overview
Protecting sensitive information is all about managing your cyber risk. Conducting an Information Security Risk Assessment (ISRA) or Cyber Security Risk Assessment (CSRA) is essential to proactively identify, analyse, and prioritise potential threats to data assets. This article delves into the diverse risk sources you should consider during your cyber risk assessment, drawing insights from established frameworks including:
SP 800-30 Rev. 1 Guide for Conducting Risk Assessments
ISO 27001 Annex A
ISO 27005: Guidance on managing information security risks Cybersecurity & Data Privacy Risk Management Model (C|P-RMM)
Putting USB Data Blockers to the Test
SecurityBase USB Data Blockers offer a simple yet effective solution to protect sensitive data from unauthorised access and malware attacks. To ensure the highest quality and security standards, out USB charge only adaptors undergo a comprehensive testing process to guarantee protection against juice jacking.
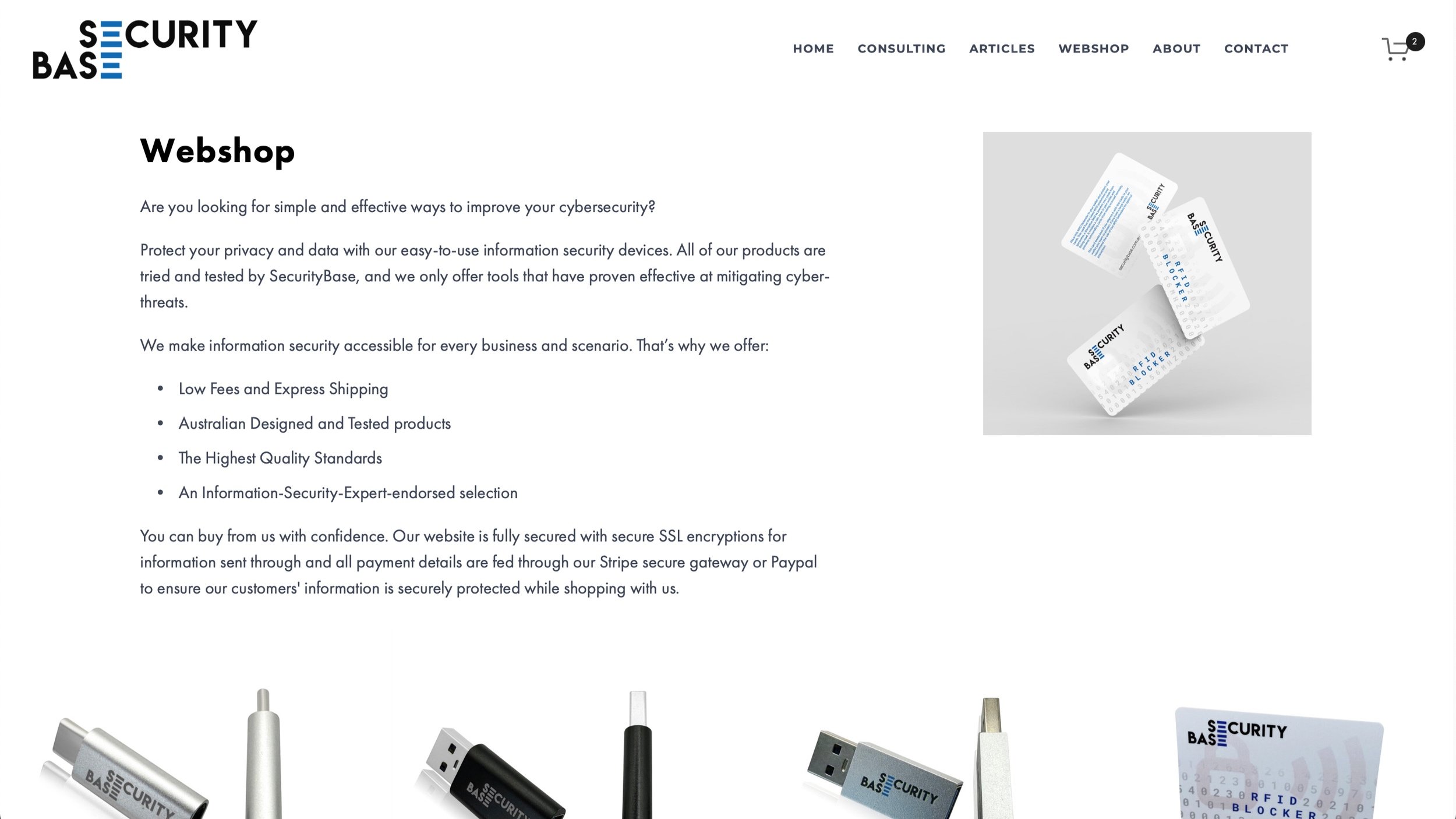
Updated Webshop with Data Privacy and Security Solutions
We have renewed our webshop to support you to simply and effectively improve your cybersecurity. We added several new features, including product reviews and a new line of USB Data Blockers to help you protect yourself from increasing cyber threats.
Cyber Security Standards and Frameworks - overview 2023 update
A solid foundation for cyber security is found in several standards and frameworks. Popular are the ISO 27001 (ISMS) from ISO International, the lSM and Essential Eight from the Australian Cyber Security Centre (ACSC), and SOC2 from the American Institute of CPAs (AICPA). But what standard suits your organisation best?
Secure USB charging: Protect Your Digital Life
Juice jacking, or a charging attack is used by hackers to gain access to your mobile phone, tablet, camera or laptop. This article has tips to prevent this type of attack using a USB Data Blocker and following some simple guidelines. USB Data Blockers: your first line of defense against juice jacking and USB hacking
Safe Travels: Protecting Yourself from Passport and Credit Card Scanning
The digital age brings incredible convenience but also introduces new security challenges. Contactless technology makes travel and everyday purchases smoother but also creates vulnerabilities for personal information. We delve into the risks of scanned passports and credit cards and explore solutions like RFID blockers to keep your data safe.
How Cyber Hygiene Can Keep You Safe in 2023: 8 Tips
Cyberhygiene is the first line of defence against hackers and cyber-attacks. Good cyberhygiene consists of simple daily routines, good procedures, and periodic check-ups to make sure your online health is in optimal condition.