Phone Privacy Screens: Smart Mobile Security
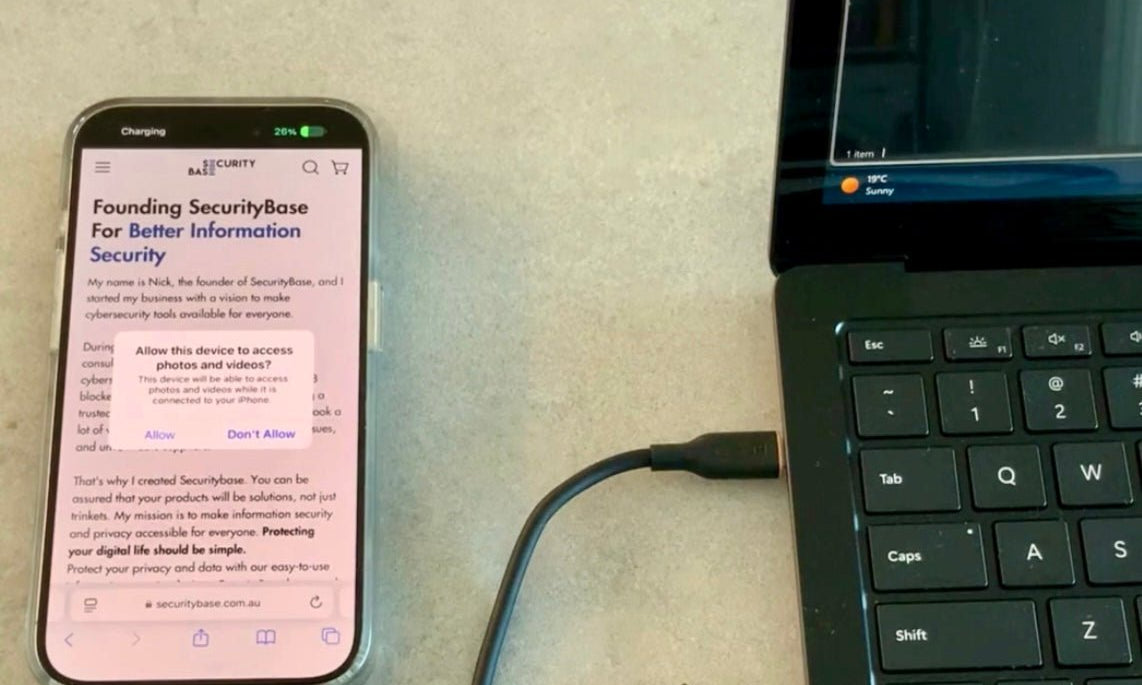
Sensitive emails, banking details, and private messages are at risk from visual hacking. A phone privacy screen offers crucial protection, limiting viewing angles and keeping your data safe. SecurityBase provides high-quality, easy-to-install privacy screens that...